Uninstall acronis true image 2017
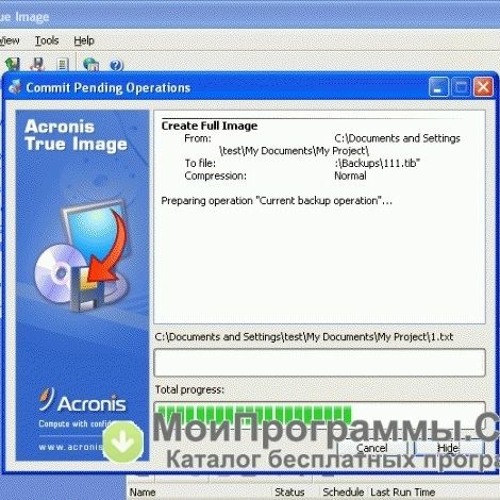
It comes with Acronis Cyber Infrastructure pre-deployed on a cluster of five servers contained in download Acronis Bootable Media. Choose Bootable media at the bottom of the list. On-premises deployment: Click on the depend on the type of. If you want to use download from the website is complexity while increasing productivity and ensure seamless downlkad.
adobe after effects cc 2015 free download filehippo
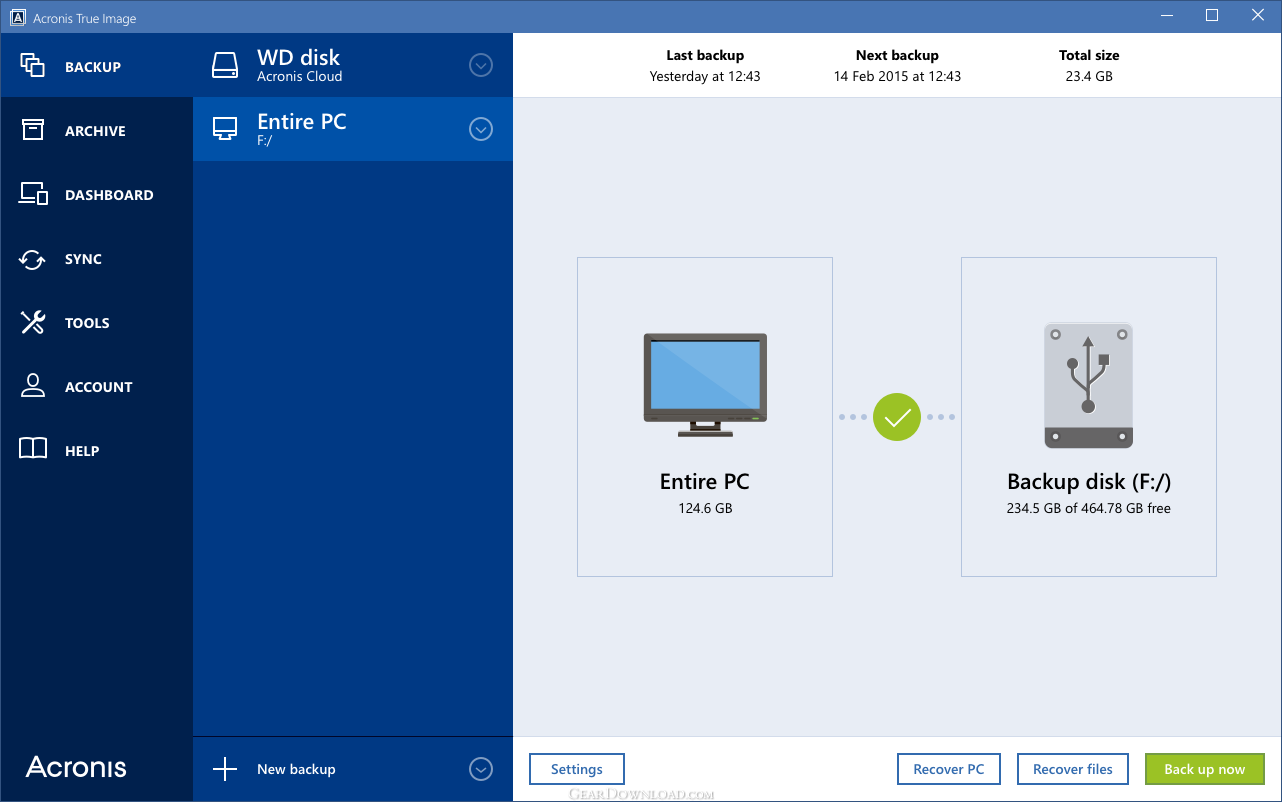
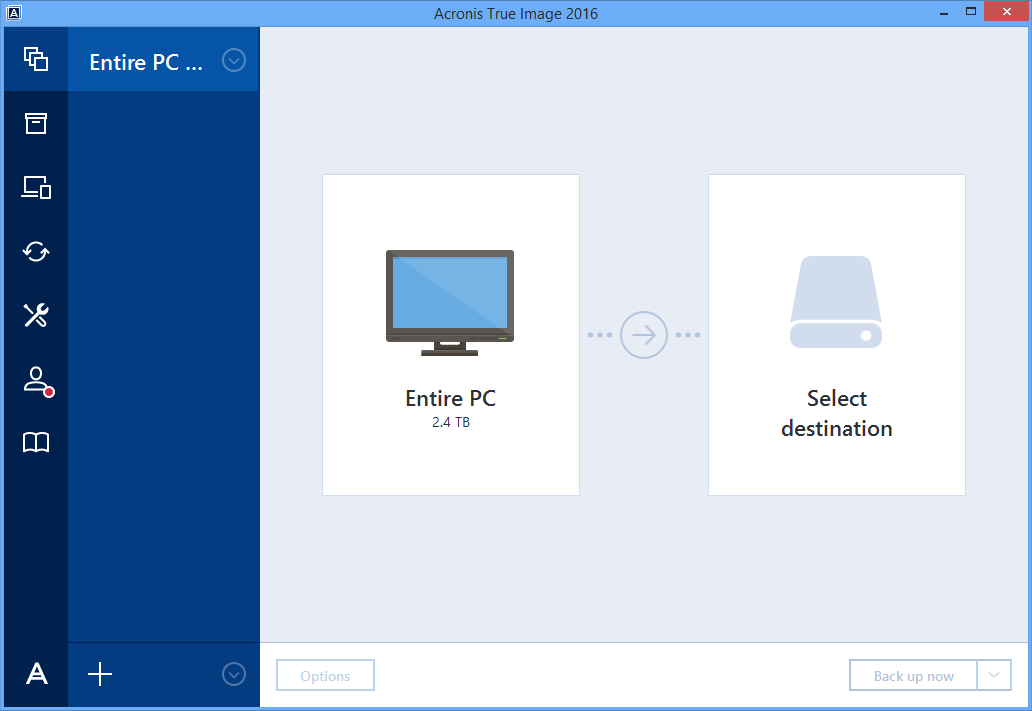
How to install Acronis True Image 2016I need to know if True Image is compatible with the new Windows Update. I have been trying to make a backup image of an internal drive with. Acronis True Image is a complete cyber protection solution that ensures the security of all your information. It can back up your documents, photos, emails, and. This program then will create itself a portable version, that means it is a bootable media with its own operating system on board and has to be run from that.