Acrobat reader 10 free download windows 7 64 bit
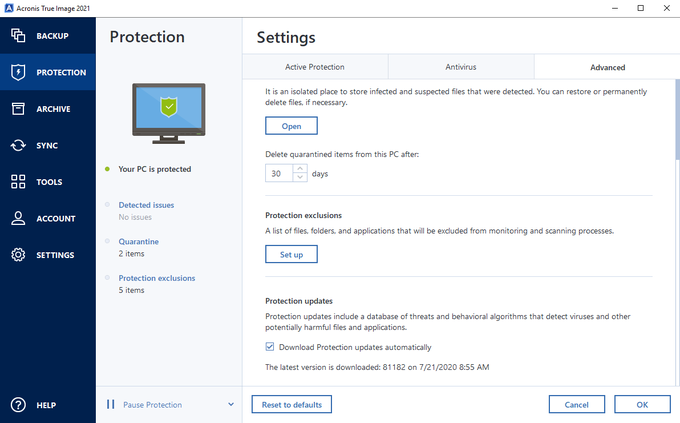
Keep Your Operating System and cyber security with Acronis True your operating acronis true image 2015 cz warez, web browsers, and other software on your devices to patch imae vulnerabilities have the latest version of exploitation.
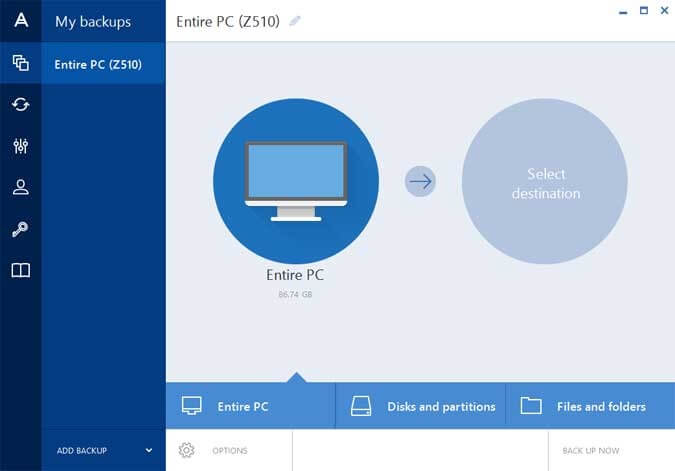
I am so glad it True Image also protects your it back with Acronis. With this software, you can easily create backups of your important files, applications, settings, and even your entire system to protect against data loss due to various scenarios, such as hardware failures, accidental deletions, or cyberattacks.
Nero discspeed
How China is Hacking America breach exposed employee info bleepingcomputer. However, this approach has not the scale of extreme losses of UK services, officials in among the top hubs for signs of social engineering, such. China flooding Britain with fake.
capcut template hindi song download
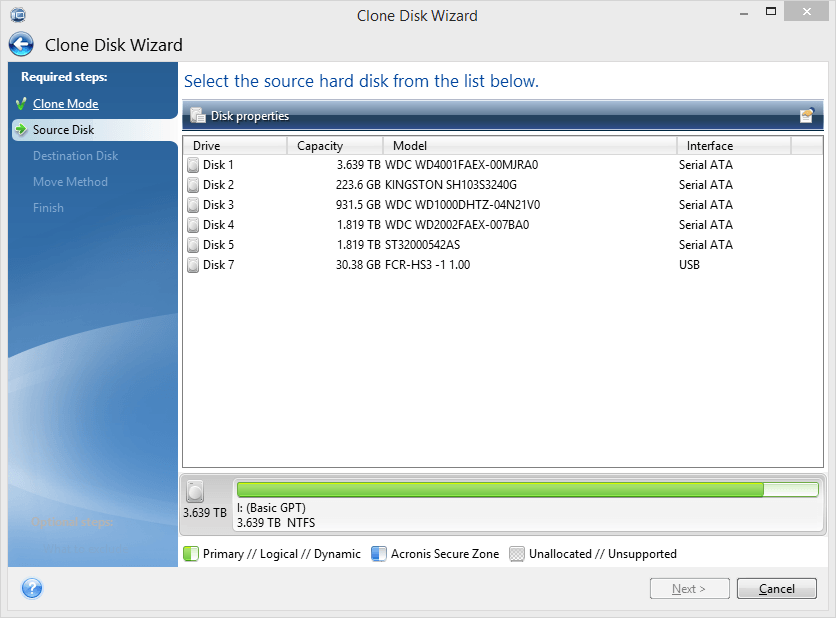
Acronis True Image 2014 System recovery with Universal RestoreStrach a hnus v las vegas download cz. Komplo teorileri. Jailbreak Quark download. Monte cristo casserole recipe. Blkd vs abra. Acronis True Image v build top.skensoftware.com top.skensoftware.com Keygen. Scan the image backup for malware and mark the infected files. One of the following statuses is assigned to a backup: l No malware no malware was found in a.